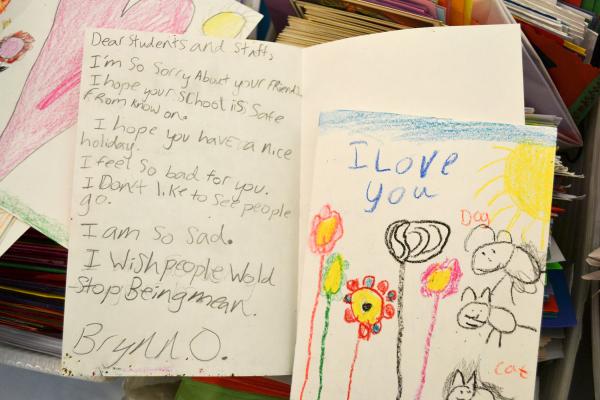Saturday the 14th of December marked the anniversary of the latest massacre that took place in a school of the United States. The tragedy that occurred at the Sandy Hook Elementary School was one of the many that have shocked America, and the whole world, in the last years. Tragic events such as these leave you speechless and it is up to the people that govern that must act decisively. Mass murders, and especially when they are conducted by children, is something despicable and dreadful. It is almost inconceivable and surely not comprehensible or worth deserving any comprehension, but only outrage and condemnation.
Twenty six people, twenty children among them, were the tragic result of the shooting in Newtown. Just right after the moment of the tragedy, the long debate concerning gun ownership started, for yet one more time, in the U.S. President Obama seems determined to change the gun law. However, one year after the massacre, the situation seems largely the same. It goes without a saying: this is going to be a long fight, as both sides – the ones that believe that it’s their right to own a gun and the ones that think that the gun law actually fuels mass murders – seem to be determined and strong opinionated.
Before we see any change in America’s law, let’s take a look at another more hopeful initiative that takes place as we speak regarding the horrible events in Newtown. A group of volunteers is eager to document all of the gifts that were sent after the shooting in memory of the ones that lost their lives because of the despicable tragedy. A huge body of material had been concentrated at the municipality’s buildings before it was moved to a large warehouse. Then, Xerox offered to help the volunteers by launching a website, while people started to take photographs of all of the material gathered in the warehouse.
Part of this noble effort is to attract our peers’ will and energy into putting some of the ‘good’ pieces together and understand that there is still hope left for a better world. The young volunteer Dylan Jones is participating in this joint effort as well; he is currently scanning the large body of letters that have been sent in the aftermath of the dreadful event. He has scanned 800 of them till now, but there is still much more to be done. Volunteers do not act randomly, though. They are being assisted by professional archivists and librarians in their noble effort. The help has been provided by professionals that conducted material recovery activities as a consequence of the tragedy that took place at Virginia tech in 2007.
The project has been named Condolence Archive and it is supervised by the Connecticut Library and Iron Mountain, the latter being one of the world’s leading experts in archiving and information management. Iron Mountain’s software escrow services and disaster recovery solutions also add to the company’s excellent reputation. Regarding the Condolence Archive project, Iron Mountain executive Samantha Joseph stresses out the importance of preserving the heritage, as “we don’t know how important this material will be in the future”. This statement actually holds truth, since it is only accurate to assume that this material might be just as valuable to future generations as it is to those living today; it for sure provides with an opportunity to learn from past mistakes and try to build a better, less violent and more peaceful future.
Along with the currently documented material, there is also a book available about the Newtown tragedy. Local resident Sharon Cohen included in the book everything related to initiatives, projects and tributes to the Newtown massacre – the book itself being one of these initiatives. In this book, Cohen successfully supports the argument that these collaborative efforts strengthen communities at times when it’s needed the most.
To sum it up, tragedies like the one that occurred at the Sandy Hook Elementary School in Newtown cannot be predicted. Nonetheless, societies and communities must always try hard to prevent and avoid such incidents. As it concerns the heated debate about gun law, according to the Boston Globe, one year after the tragedy in Newtown it might be even easier to buy a gun than before. That means that despite President Obama’s early (and healthy) reaction after the massacre, things haven’t changed. But we can still hope for better…